What Is Sha 256 Encryption Password Based Key Derivation SHA 256 hash enhances security in deriving encryption keys from passwords with salt and iterations Secure File Transfer SHA 256 hash ensures integrity in secure file transfer protocols by validating hash values
SHA 256 part of the SHA 2 algorithm family is a Secure Hash Algorithm introduced collaboratively by the NSA and NIST in 2001 It emerged as a robust successor to the SHA 1 family which faced increasing vulnerabilities to brute force attacks SHA 256 is a member of the SHA 256 family SHA 3 is a different hash function Designed by the Keccak Team through an open competition organised by the NIST No known vulnerabilities as of current date Variable with the most common being the 1600 bits Variable with standard output size being 224 256 384 or even 512 bits
What Is Sha 256 Encryption

What Is Sha 256 Encryption
https://i.ytimg.com/vi/ezbGw2dwLg4/maxresdefault.jpg

TLS Essentials 3 Confidentiality With AES RSA Hybrid Encryption
https://i.ytimg.com/vi/6YT0Anpab4g/maxresdefault.jpg

What Is AES 256 Bit encryption In 2 Mins Simplest Explanation Of AES
https://i.ytimg.com/vi/AOgvutSpy3o/maxresdefault.jpg
Secure Hash Algorithm 256 bit also known as SHA 256 is a cryptographic hash function that converts text of any length to an almost unique alphanumeric string of 256 bits The output is known as a hash value or hash What is the SHA256 Encryption SHA stands for Secure Hash Algorithm and SHA 256 is a member of the SHA 2 family of encryption algorithms The NSA and NIST worked together to create this encryption technique which was first used in 2001 as a replacement for the SHA 1 family which was starting to fall victim to brute force attacks
SHA 256 which stands for Secure Hash Algorithm 256 is an algorithm in the family of cryptographic hash functions It s like the secret sauce in your grandma s recipe unique and integral to the process But unlike grandma s sauce this algorithm has nothing to do with food SHA 256 is a part of the SHA 2 family of algorithms where SHA stands for Secure Hash Algorithm Published in 2001 it was a joint effort between the NSA and NIST to introduce a successor to the SHA 1 family which was slowly losing strength against brute force attacks
More picture related to What Is Sha 256 Encryption
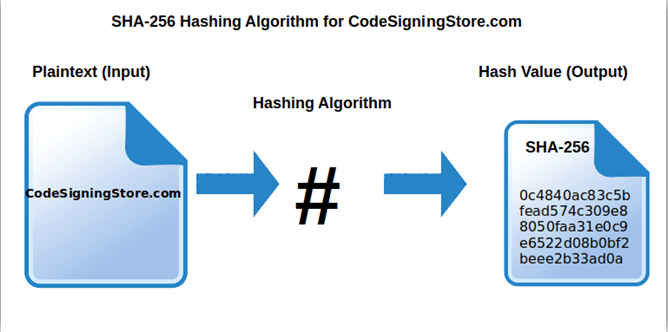
Hash Algorithm Comparison MD5 SHA 1 SHA 2 SHA 3 42 OFF
https://codesigningstore.com/wp-content/uploads/2023/02/sha-256-hashing-algorithm.png

Hash Function Pid
https://sectigostore.com/blog/wp-content/uploads/2022/04/sha-256-algorithm-feature-image.jpg
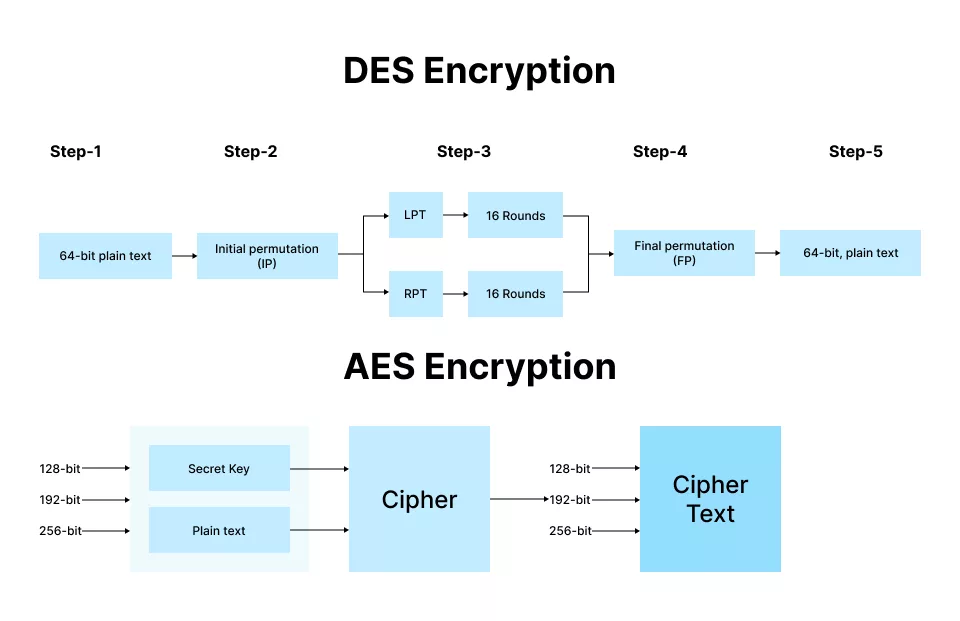
RSA AES Encryption Key Differences Explained 54 OFF
https://cheapsslweb.com/blog/wp-content/uploads/2023/03/RSA-vs.-AES-Encryption_-Key-Differences-Explained-1-jpg.webp
SHA 256 generates a 256 bit 32 byte signature Toward the end of this article I ll break down each step of SHA 256 s cryptographic algorithm and work through a real example by hand If you re interested in learning cryptography with hands on code examples you can also check out my Learn Cryptography course on Boot dev Secure Hashing Algorithm or SHA Data and certificates are hashed with SHA a modified version of MD5 By using bitwise operations modular additions and compression functions a hashing algorithm reduces the input data into a smaller form that is impossible to comprehend Can hashing be cracked or decrypted you may wonder
[desc-10] [desc-11]
Qu Es SHA 256
https://academy.bit2me.com/wp-content/uploads/2018/07/18_Sha256-1.png
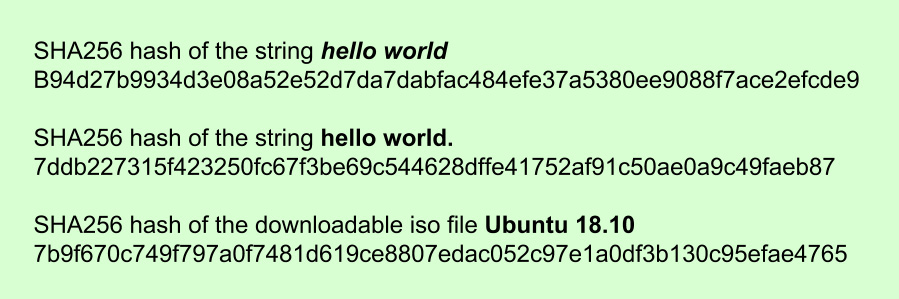
What Is SHA 256 Algorithm Minerium
https://minerium.com/wp-content/uploads/2022/11/SHA256-Hash-Samples.jpg

https://debugpointer.com › security
Password Based Key Derivation SHA 256 hash enhances security in deriving encryption keys from passwords with salt and iterations Secure File Transfer SHA 256 hash ensures integrity in secure file transfer protocols by validating hash values

https://www.encryptionconsulting.com › education-center
SHA 256 part of the SHA 2 algorithm family is a Secure Hash Algorithm introduced collaboratively by the NSA and NIST in 2001 It emerged as a robust successor to the SHA 1 family which faced increasing vulnerabilities to brute force attacks
256 Telegraph

Qu Es SHA 256
Rsa256

SHA 256 Algorithm N able

SHA 256 Secure Hash Function IP Core

What Is The SHA 256 Algorithm And How Does It Work NordVPN

What Is The SHA 256 Algorithm And How Does It Work NordVPN

Sha 256 Hash Calculator Bezyclassifieds
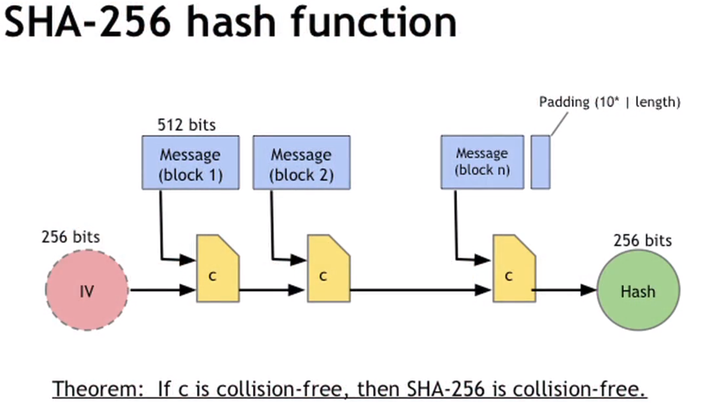
SHA256

Introduction To SHA 256 RugDoc Wiki
What Is Sha 256 Encryption - What is the SHA256 Encryption SHA stands for Secure Hash Algorithm and SHA 256 is a member of the SHA 2 family of encryption algorithms The NSA and NIST worked together to create this encryption technique which was first used in 2001 as a replacement for the SHA 1 family which was starting to fall victim to brute force attacks